Is Your Wi-Fi as Secure as You Think? An Overview of Wi-Fi Security Standards
Category : Cyber Security Technology
Wi-Fi is a wireless networking technology that allows devices to connect to the internet using radio waves. Wi-Fi security is the protection of data transmitted over wireless networks. As Wi-Fi technology has evolved, so have the security protocols that protect it.
There are several standards for Wi-Fi, which are denoted by the numbers “4”, “5”, and “6”. These numbers refer to the generation of the Wi-Fi standard, with newer generations offering faster speeds and more advanced features than older ones.
- Wi-Fi 4, also known as 802.11n, was released in 2009 and operates in the 2.4 GHz and 5 GHz bands. It has a maximum theoretical data transfer rate of 600 Mbps and uses multiple-input multiple-output (MIMO) technology to improve range and performance.
- Wi-Fi 5, also known as 802.11ac, was released in 2014 and operates only in the 5 GHz band. It has a maximum theoretical data transfer rate of 3.5 Gbps and uses MIMO technology, as well as beamforming to improve range and performance.
- Wi-Fi 6, also known as 802.11ax, was released in 2019 and operates in the 2.4 GHz and 5 GHz bands. It has a maximum theoretical data transfer rate of 9.6 Gbps and uses MIMO technology, as well as orthogonal frequency-division multiple access (OFDMA) to improve range and performance. It is also designed to be more efficient and able to support more devices simultaneously than previous generations.
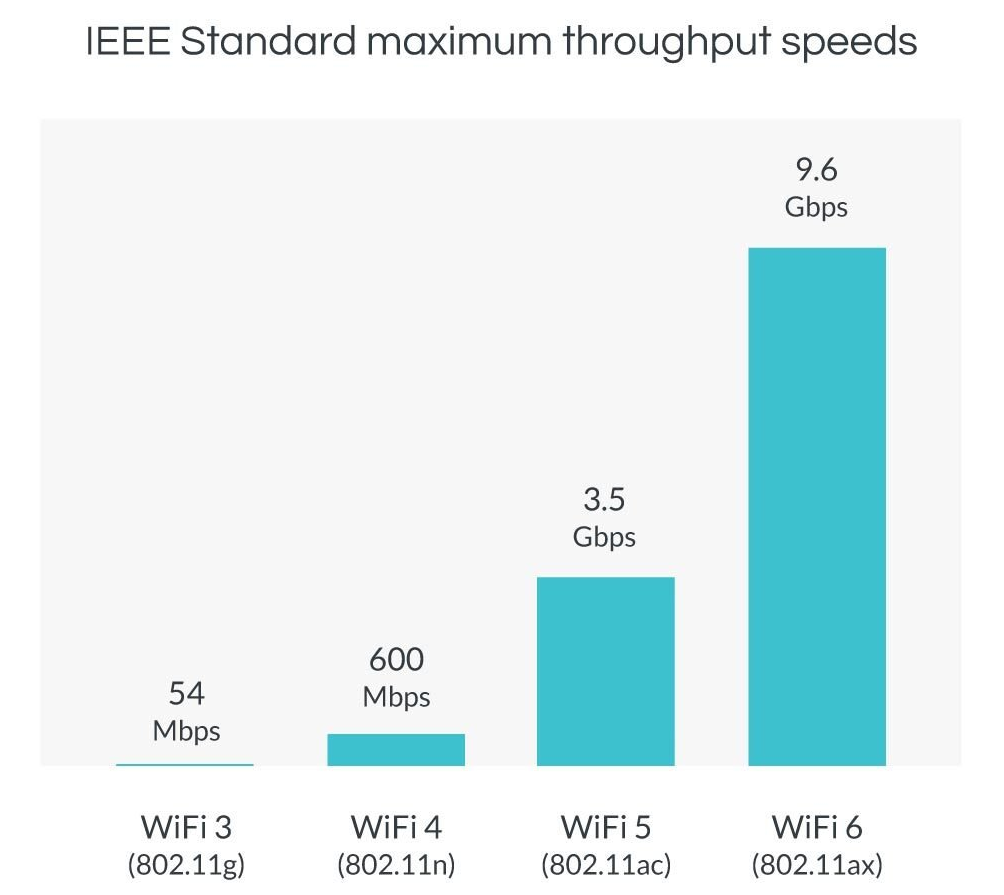
Newer Wi-Fi standards offer faster speeds and better performance than older ones. However, to take advantage of these improvements, both the device and the Wi-Fi router must support the same standard.
It is important to note that while newer Wi-Fi standards offer improved security measures, no security protocol is foolproof. It is always a good idea to use strong passwords, enable two-factor authentication, and keep your devices and router software up to date to protect your Wi-Fi network.


Recent Comments