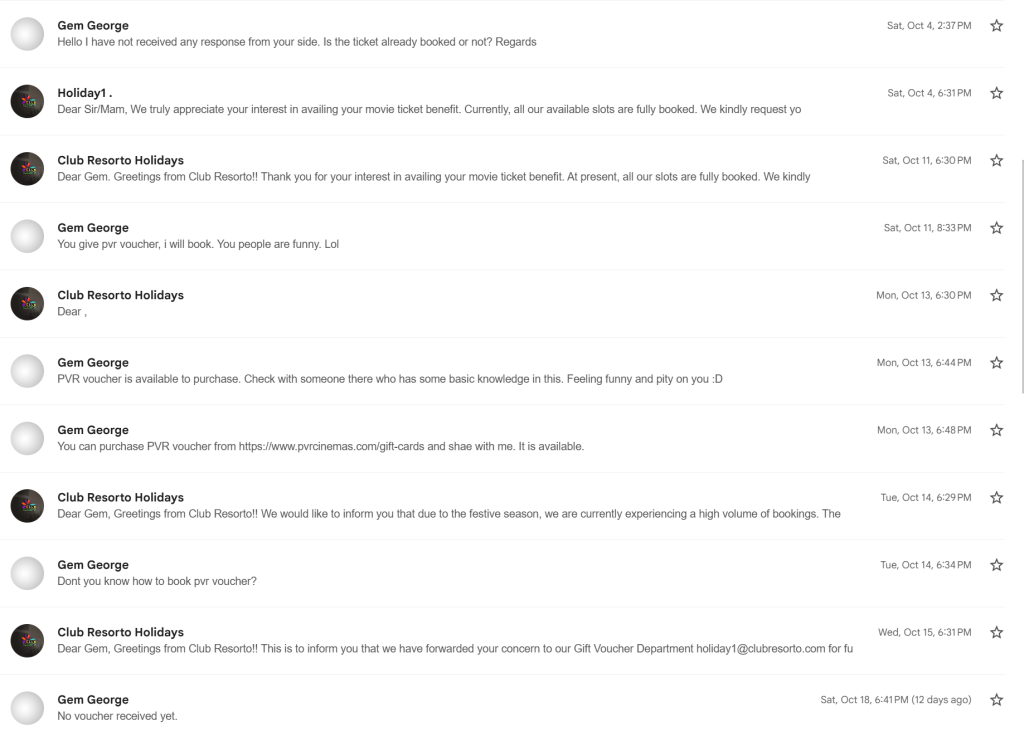
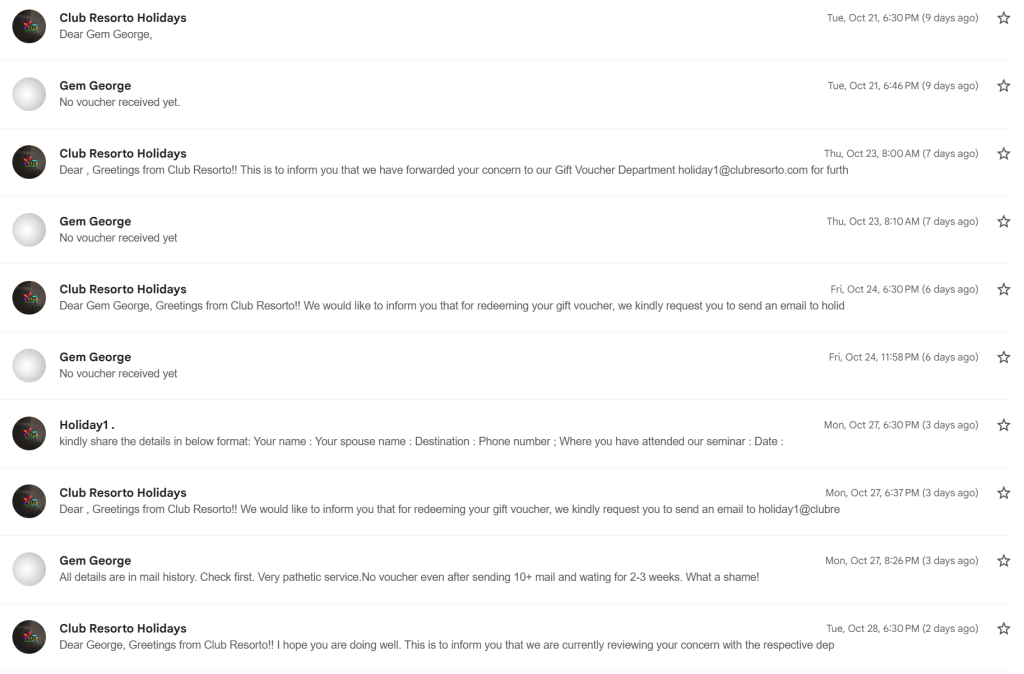
Niyo Referral Code GEMGE520 – Get ₹250 in Niyo Coins as Joining Bonus
Category : Guest Post
If you’re looking for a simple, rewarding way to start your Niyo journey, you’re in the right place. In this post, I’ll share how you can use the Niyo referral code GEMGE520 to grab ₹250 in Niyo Coins as a joining bonus and why Niyo is worth checking out.
What Is Niyo?
Niyo is a modern digital banking platform that offers app-based money management, travel-friendly accounts, and rewards on your everyday spending. Instead of visiting a branch, most things are handled right from your phone – from opening an account to tracking your expenses.
Niyo Referral Code: GEMGE520
Here’s the star of the show:
Use Niyo Referral Code: GEMGE520
Get: ₹250 in Niyo Coins as a joining bonus
You can enter this referral code while signing up in the Niyo app to claim your reward (subject to Niyo’s current offer terms and eligibility).

How to Use the Niyo Referral Code GEMGE520
Follow these simple steps to get started:
1. Download the Niyo App
Go to the Google Play Store or Apple App Store and search for “Niyo”.
2. Sign Up / Create Your Account
Open the app, enter your mobile number, and start the registration process.
3. Enter the Niyo Referral Code
When you see the “Have a referral code?” or similar option, enter:
GEMGE520
4. Complete Onboarding (KYC, if required)
Follow the on-screen instructions to complete your basic and, if needed, full KYC as per Niyo’s process.
5. Get Your Joining Bonus
Once your account is successfully created and the referral is validated as per Niyo’s terms, you’ll receive ₹250 in Niyo Coins in your account/rewards section.
FAQ
1. What is the best Niyo referral code right now?
If you’re signing up, you can use Niyo referral code GEMGE520 to get ₹250 in Niyo Coins as a joining bonus (subject to Niyo’s terms and ongoing offer).
2. Where do I enter the Niyo referral code?
You can enter the referral code during the signup/registration flow in the Niyo app, usually where it asks “Have a referral code?” or similar.
3. Is the Niyo referral bonus guaranteed?
The bonus is provided as per Niyo’s current referral policy, eligibility criteria, and offer validity. Make sure you:
Enter the code GEMGE520 correctly -> Complete the KYC / onboarding -> Follow any additional steps Niyo may require
4. Do I need to pay anything to use the referral code?
Entering a referral code like GEMGE520 is typically free. Any charges depend on the specific Niyo product or card you’re opting for as per Niyo’s own terms.



Recent Comments